Configure Single Sign-On (SSO)
Destiny offers SSO access via the following:
- Clever SSO
- IMS Global Learning Consortium's Learning Tools Interoperability® (LTI) Standard
- Security Assertion Markup Language (SAML)
| Note: An SSL Certificate configured for the Destiny server is required for a successful self-hosted LTI SSO setup via Classlink, Clever, Canvas, Schoology, and any other SSO option. |
Clever SSO
With Destiny version 18.3 or higher, your district can use Clever SSO. Destiny must be:
- Internet accessible
-
SSL enabled
Note: SSL is already enabled for all Destiny Cloud customers.
You will need to gather the following information:
|
Note: After you have all the information, contact Destiny Technical Support (888-511-5114, option 2 or techsupport@follettlearning.com) to complete the setup. |
-
Email addresses that Clever uses for patrons in their Destiny patron record. The email address can be in any of the following Destiny patron fields, as long as it is in the same field for all patrons you want to authenticate using Clever SSO. For example, if the email address for faculty is Email 1, students must also use Email 1.
- District ID
- Email 1
- Email 2
- User Name
- Barcode
- User Defined 1
- User Defined 2
- User Defined 3
- User Defined 4
- User Defined 5
-
Clever District ID, which you get when you perform the setup on your Clever portal.
Notes:
- You must gather this information before Follett School Solutions, LLC can proceed with the SSO integration.
- Follett does not have access to this information – you must get it from Clever directly.
- Contact Clever if you need help with this part of the setup.
SSO with Google
To set up Google authentication in Destiny, you first need to configure your district’s Google for Education account. This involves creating credentials in the Google Developer Console API Manager at: https://console.developers.google.com/apis/dashboard.
| Note: If you do not have a district Google for Education account, use Follett's account to authorize the connection. |
To configure Google SSO in Destiny:
|
Notes to Follett Cloud customers:
|
- Log in as the Destiny Administrator.
- Select Setup > Sites sub-tab.
- Next to the district name, click
 .
. - Next to SSO Configuration, click Configure.
- On the Single Sign-On Configuration page, click New.
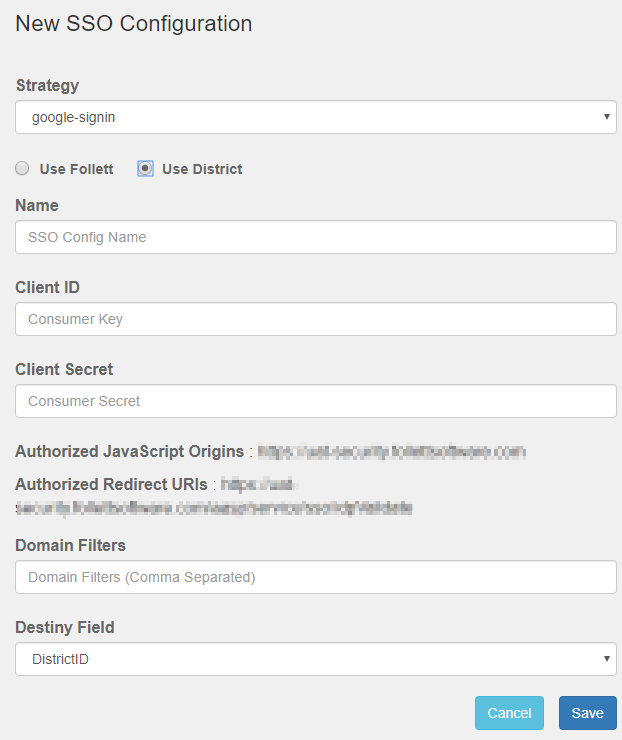
- From the Strategy drop-down, select google-signin.
- Choose one of the following options: Use Follett or Use District.
- In the Name field, type an SSO Config Name of your choice.
- If you selected Use Follett, the Client ID and Client Secret fields are not shown (go to Step 10). If you selected Use District, complete the following fields:
- Client ID: Type the Consumer Key you created in the Google Developer Console API Manager.
- Client Secret: Type the Consumer Secret you created in the Google Developer Console API Manager.
- Domain Filters: If your Destiny username claim fields do not contain a domain name, type the domain name in this field. If the claim sent to Destiny matches the Destiny username claim field, leave this field blank.
Example: If the Google claim field is jennystudent@school.com and the Destiny claim field is jennystudent, you would identify the Domain Filter as school.com.
- In the Destiny Field drop-down, select the field that corresponds with the username claim field.
- Click Save.
- If you are a Follett Cloud customer, contact Follett Technical Support to complete the setup.
| Note: District-level and site-level users are routed to the appropriate site when logging in. For example, a district user with site-level access can log in at both the site and district levels, and switch between the two. However, if a district user without site access logs in at the site, they are routed to the district. If a site user logs in at the district, they are routed to the appropriate site. For more details, see Access Levels and Permissions. |
SSO with IMS Global Learning Consortium's LTI Standard
If your district uses a learning platform that is compliant with LTI, you can access Destiny resources and links without ever signing in to Destiny.
Leveraging the LTI standard supports seamless integration and single sign-on access to Destiny and Destiny resources from compliant K-12 learning platforms, such as learning management systems, portals and dashboard providers.
For background information on the LTI specification, visit: https://www.imsglobal.org/activity/learning-tools-interoperability
To generate LTI configuration information:
|
Notes to Follett Cloud customers:
|
- Log in as the Destiny Administrator.
- Select Setup > Sites sub-tab.
- Next to the district name, click
 .
. - Next to SSO Configuration, click Configure.
- On the Single Sign-On Configuration page, click New.
- From the Strategy drop-down, select lti. The Key, Secret and Endpoint fields are populated automatically.
- In the Name field, type a name of your choice.
- From the Claim Names drop-down, select the field that claims your identifier.
- From the Destiny Field drop-down, select the Destiny field that corresponds with the Claim Name.
- Click Save.
- If you are a Follett Cloud customer, Follett Technical Support to complete the setup.
After you generate the LTI configuration information in Destiny, refer to the instructions provided by your learning platform provider to configure Destiny as an LTI tool. Following is a list of commonly-used learning management systems:
- Blackboard®
- Canvas
- ClassLink, Inc.
- Desire2Learn
- Its Learning
- Moodle™
- Schoology™
Single Sign-On with Security Assertion Markup Language (SAML)
Many school computer networks are set up so that students and staff access technology resources with a username and password. SAML SSO enables Destiny to use the same system. Once the standard is implemented, students and teachers no longer need to remember multiple usernames and passwords to access Destiny.
Setting Up SAML SSO
Deploying SAML SSO for Destiny requires the involvement of Follett’s Implementation Services team and your district IT staff. If you are interested in setting this up for your district, contact Follett Technical Support. Your district’s IT resource should be prepared to provide information about your district identity provider.